ESET Endpoint Security for Windows and Mac
Comprehensive multilayered security, combining machine learning and human expertise

Sorry, this product is no longer available, please contact us for a replacement.
Overview:
ESET Endpoint Security for Windows
Award-winning ESET NOD32® technology delivers superior protection against advanced malware with a light footprint and unmatched speed to:

Protect against ransomware

Block targeted attacks

Prevent data breaches

Prevent zero-day attacks
Management server
ESET Security Management Center manages endpoint products from a single pane of glass and can be installed on Windows or Linux. As an alternative to on-premise installation, customers with up to 250 seats can manage their endpoints via ESET Cloud Administrator.
Machine learning
All ESET Endpoint products currently use machine learning in conjunction with all of our other layers of defense and have done so since 1997. Specifically, machine learning is used in the form of consolidated output and neural networks. For a deep inspection of the network, admins can turn on the special aggressive machine learning mode that works even without internet connection.
Multilayered defense
A single layer of defense isn't sufficient in today's constantly evolving threat landscape. All ESET endpoint products have the ability to detect malware pre-execution, during execution and post-execution. By focusing on the entire malware lifecycle, ESET provides the highest level of protection possible.
Benefits:
The ESET difference
Behavioral Detection - HIPS
ESET's Host-based Intrusion Prevention System (HIPS) monitors system activity and uses a pre-defined set of rules to recognize and stop suspicious system behavior.
Ransomware Shield
Monitors and evaluates all executed applications based on their behavior and reputation. Designed to detect and block processes that resemble the behavior of ransomware.
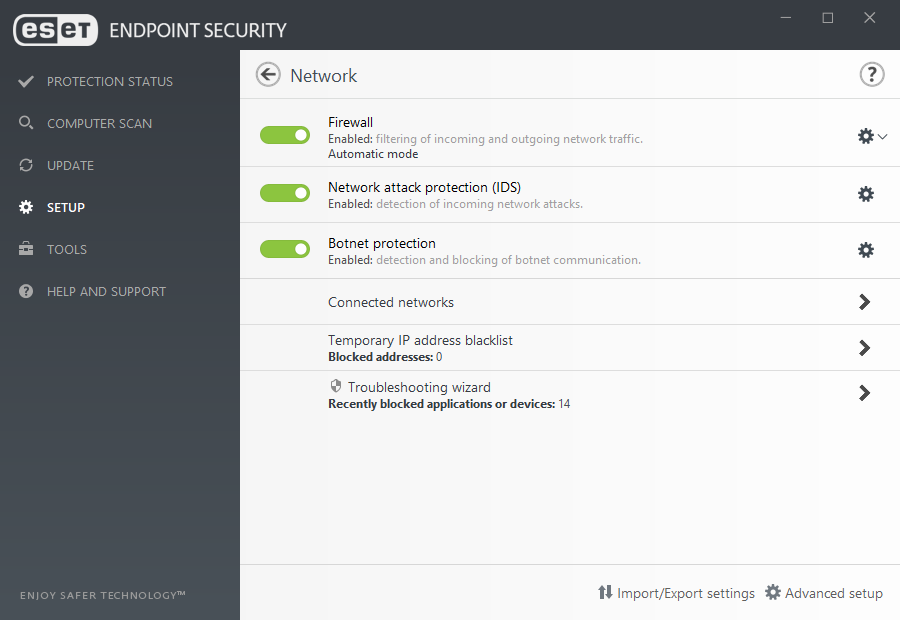
Network Attack Protection
ESET Network Attack Protection improves detection of known vulnerabilities on the network level. It constitutes another important layer of protection against spreading malware, network-conducted attacks, and exploitation of vulnerabilities for which a patch has not yet been released or deployed.
Advanced Memory Scanner
A unique ESET technology which effectively addresses an important issue of modern malware—heavy use of obfuscation and/or encryption. Advanced Memory Scanner monitors the behavior of a malicious process and scans it once it decloaks in memory.
In-product sandbox
ESET’s In-product sandbox assists in identifying the real behavior hidden underneath the surface of obfuscated malware. Utilizing this technology, ESET solutions emulate different components of computer hardware and software to execute a suspicious sample in an isolated virtualized environment.
Exploit Blocker
ESET Exploit Blocker monitors typically exploitable applications (browsers, document readers, email clients, Flash, Java, and more) and instead of just aiming at particular CVE identifiers, it focuses on exploitation techniques. When triggered, the threat is blocked immediately on the machine.
Two-way firewall
Prevents unauthorized access to the company network. It provides anti-hacker protection, data exposure prevention, and enables defining trusted networks—making all other connections, such as to public Wi-Fi, restricted by default.
Botnet Protection
ESET Botnet Protection detects malicious communication used by botnets, and at the same time identifies the offending processes. Any detected malicious communication is blocked and reported to the user.
Reputation & cache
When inspecting a file or URL, before any scanning takes place, our products check the local cache for known malicious or whitelisted benign objects. This improves scanning performance.
ESET LiveGrid
Whenever a zero-day threat such as ransomware is seen, the file is sent to our cloud-based malware protection system, LiveGrid®, where the threat is detonated and behavior is monitored. Results of this review are provided to all endpoints globally within minutes without requiring any updates.
Looking for more?

Upgrade to full-service protection
ESET Secure Business Cloud
As well as protecting all your computers, laptops, and file servers, make your email gateway impenetrable. ESET mail security eliminates email-borne malware at the server level, before it can do any damage.
- Cloud-based management
- Endpoint security
- File server security
- Mail security

Add data access protection
ESET Secure Authentication
A simple, effective way for businesses of all sizes to implement multi-factor authentication across commonly utilized systems.
- Prevent data breaches
- Meet compliance requirements
- Easily manage authentication

ESET Dynamic Endpoint Protection
- Security Management Center
- Endpoint Protection Platform
- Cloud Sandbox Analysis
System Requirements:
Operating Systems:
- Microsoft Windows 10
- Microsoft Windows 8.1
- Microsoft Windows 8
- Microsoft Windows 7
- Microsoft Windows Vista
- Microsoft Windows XP
- macOS 10.9 and later
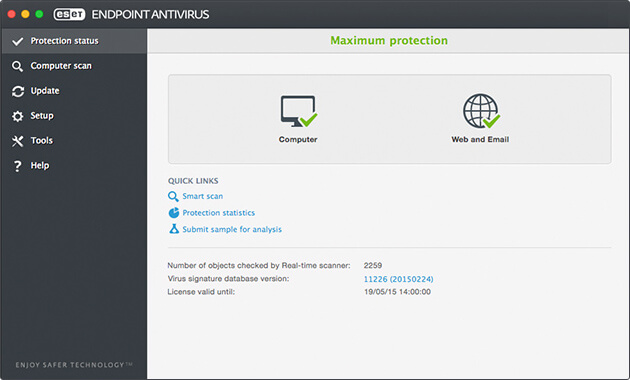
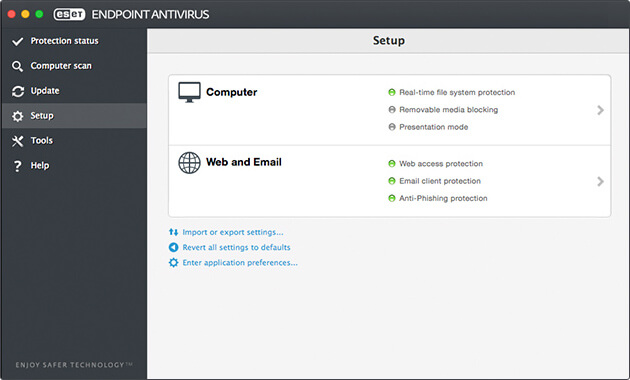
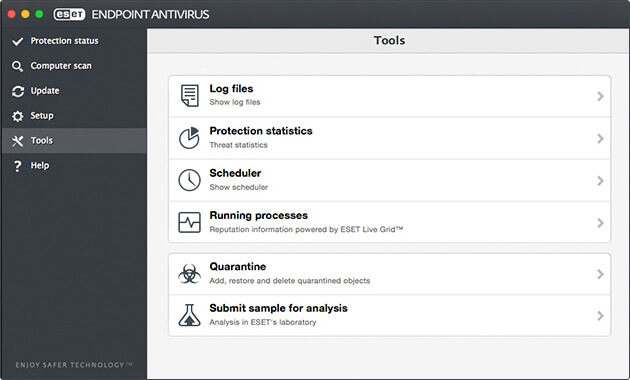
Screenshots:
Documentation:
Download the ESET Endpoint Solutions Overview (PDF).
Download the ESET Endpoint Security for Windows Datasheet (PDF).
Download the ESET Endpoint Security for Mac Datasheet (PDF).